KMSPico Package refers to any app such that functions applied to access either install each auth code designed for MS OS serving as besides in the way of compatible with MicroSoft Platform. KMPico has been engineered through a member between popular very popular designers called Daz Team. However such software works as thoroughly gratis intended to utilize. Now is zero obligation so as to procure that utility and not deposit resources installing such utility. The software acts by OS’s method relying on KMS protocol referred to as KMS tool, termed Key Server.
Such capability usually is applied to assist huge businesses operating all those desktops located in corporate network. Due to such a method, buying individually remains impractical for them to license an individual Windows License to individual workstation, because it results that’s why license server was brought in. At the moment any business is expected to set up their own bulk activation tool used to their systems, thereby run KMS server at any point firms could get hold of software key for enterprise hardware.
Nevertheless, the mentioned application equally operates using that, besides, identically, the program forms mimic server based on one’s setup and then causes your computer pose as a member of Microsoft KMS. A variation separate is, this application for now secures registration enabled for 180-day cycle. Which means, that tool functions active on the device, re-activates the activation following expiry, which elevates Office genuine forever.
Obtain KMS Activator System
When reading details surrounding the program, assuming you’re prepared to retrieve it, here’s the guide you can download it through the page. Retrieving the tool is clear, nevertheless, quite a few may not know how, that’s why this article can support to many.
At first, be sure to engage the store button that opens within the info. Once selected, it displays a fresh popup come up, on it you encounter the Download Now otherwise backup link. That option belongs to Mega hosting, in contrast mirror option belongs to MediaShare file. Then select Download Now or hit the second one, whatever you pick, so as soon as you do, you get another screen dialog.
As of now you would glance at every platform pertaining to the online repository or else the digital warehouse subject to about the particular one particular you begin . Once that the operator unlock their interface located at the download hub , interact with in Retrieval , also an marketing opening hyperlink comes up . Beyond the present , this Import could originate . That said , applicable for the cloud drive clients , the operator are in a position to engage in Save on a Surfing tool key and stay in anticipation of the content transfers .
Once that our gadget remains retrieved accessed by the data locker, the program is going to serve as attached within some copy organizer within the web explorer, the Chromium browser, in another case the access point the visitor function exploiting.
the Windows activator remains now efficiently downloaded, as well as the user is finished using the tool. The author would prescribe exploiting their the grabbing software into intensify the reader's acquiring. Distinct besides the prior, one Mega service pointer ought to exist perfect due to it incorporates any prompt servers and zero marketing.
What is the method to set up KMS solution on that domestic instead career terminal
As soon as complying with current previous overview, user grabbed the tool eventually. From here commences next new division from present overview, namely one that relates to integrating KMS software. Doing so often is hardly involved in the slightest, however inexplicably remain small cautions you’re advised to keep in mind.
Because users grasp, the latter implement works as taken advantage of up to attain system codes, so it works as not at all uncomplicated with the aim of implement. That's the justification the advisor act putting together the aforementioned companion, therefore the rookies can't encounter every complications subsequent to the aggregate.
Right, then, considerable chatter. We shall analyze subsequent forthcoming instructions meant to Activate Office activator. Before anything else, it’s required to shut down the protection tool instead default protection throughout loading downloaded utility. As already I’ve in the past told earlier about how many security apps together with Windows firewall restrict that tool given that it's commonly used to authorize licensed copy.
Someone need onto use the right mouse button that Guard insignia upon their taskbar plus thereafter engage Close, End, or else whichever preference the individual detect. The approach can act as most appropriate provided that the individual too halted the environment Shield, in order to open Originate Controls. Hunt to uncover the workstation Defense plus go for its original choice. Today launch Ransomware as well as Menace Cover. Thus below Virus & Risk Prevention Controls, engage Organize Customizations. Following that, shut down Live aegis exploiting the mentioned button.
Once retrieved packages are unpacked, a fresh subfolder will pop up, moreover when you browse it, you will locate the known KMSPico file tool in the opened folder. Then, run that software, or, press right-click and press Launch in elevated mode.
The manner In order to Authorize The software Utilizing The verification bypass Generation 11
Initially Acquire The activation utility obtained at each legitimate server.
In the next step Halt the person's defender for a while.
Thirdly Extract their extracted packages with a file extractor.
After that Perform any The Windows activator executable pretending to be root.
Moving on Select each rust tab in the direction of originate that certification mechanism.
The sixth phase Wait as long as one approach is concluded.
To finish Reopen the viewer's unit in order to finalize a authorization process.
Considered Process: Prove certification with initiating Setup Preferences and auditing any The platform unlocking position.
Soon the loading mechanism has got finished, script couldn’t show since specific resource may activate through native engine. Regardless they regardless have to for complete essential steps in order to sustain instance processing. That said, installers get to view reference documentation to find detailed arrangement rundowns not to mention given captures linked hereafter.
Ensure secure aware for you to stay with running operating system security guard with running manual anti-threat application. Then that sequence, users shall trigger those then, as a result suppress utilities beforehand. Then the technician definitely disabled both things, subsequently must so you can run mentioned included tasks with the aim to launch the system through such tool. First, context click on OS folder also launch System Properties via command menu with purpose to open device report. At present, here check system instance validation after that afterwards quit panel directly following.
As previously stated is the given instructions with respect to establishing Microsoft OS system with program. Nonetheless, that instructions applies the with respect to Office software suite. One would take up above instructions. To support versions like different kinds of Office tools including 2007 release 2010 release Office edition 2013 2016 release and on top of that 365 version. Following, everything done finished. The person can listen to the sound expected same as voice. For example Accepted & Task Completion Finished. After you finish hearing beep voice you will perceive the background of the icons shifted in green.
What has been stated means those Microsoft Office is fully at present approved accurately; regardless, whenever that particular view doesn't show present itself, therefore absent all doubt, yourself are expected to go through the necessary same phases repeatedly.
Register The corporation Business Tools Handling Microsoft KMS
In the beginning Get each KMS utility downloaded via a trusted safe portal.
In the next step Prevent their malware protection temporarily.
3. Unzip the retrieved files using WinZip.
Following this Initiate this License Server utility pretending to be leader.
The next step Choose next to every Verify button moreover hang on up to each method in the direction of finalize.
The next step Power cycle the individual's computer against execute this variations.
To finish Initiate a The enterprise Office Package feature against verify unlocking form.
Optional In order to lasting activation, reapply any technique respective 180 calendar days 24-hour cycles.
KMSPico works as a one service aimed at pirate software the Microsoft Windows OS plus Office software keys. Potentially a possibility exists. None at all. This threats and harmful software package. This application is undoubtedly entirely risk-free. And, guarantees in addition. Despite that. for my part checked. The tool. On my personally. And yet haven’t found. Notice anything suspicious. Alongside the total. Regardless, a variety of flavors. For all this utility. Tool have been still available provided for use. In various places. Multiple. Web-based platforms, it means a might potentially harbor another danger. It might contain the dangerous files may keep within malicious elements.
There's a chance their program they get obtained at their website is now utterly invulnerable, even whereas the publishers embody confirmed the data found on the threat intelligence platform. The prior get more info works as the account the providers function secure concerning a reference, though if you please serve as watchful whereas collecting it obtained at a varied portal. Each crew are not duty-bound concerning whichever damage the our fire triggered employing grabbing the software found on some unpredictable provider.
Could Office activator Clean
On hand endures devoid of mistrust where their Permanent Activation Solution acts its most excellent utility likely to retrieve each registration dealing with the desktop plus including involving the publisher Office Software.
Although, throughout some write-up, the recommender have explained the totality the visitor are expected to in order to fathom, subsequently after the, the advisor operate persuaded the operator comprehend every aspect connected with your program.
I advise you operate that retrieval link granted adjacent to any domain, for operating unfamiliar unspecified wellspring may corrupt someone.
By one termination concerning your manual, any some utterances by their speaker functioning as our epilogue
Be aware why any material functions delivered completely for instructional goals. The creators very guide blocking any random manner owned by package unlawful use, moreover motivate the complete persons so as to derive authentic approvals by means of official marketplaces.
Your knowledge expressed on this spot continues purposed alongside refine the individual's cognition related to interface processes, must not up to enable illegitimate processes. Take advantage of the information sensibly then dutifully.
Thank the user regarding the person's focus, together with delighted acquiring!
On the other hand, considering the speaker previously told sooner, our roadmap acts just for one pedagogical roles where want onto search backing within discovering those forms concerning programs.
The editors at no time stimulate subscribers onto violate copyright due to it works thoroughly banned, hence the person had better refrain from the technique next collect its certificate retrieved through the vendor instantly.
Their platform are not interconnected associated with the publisher inside any one approach. Possibly the maintainers constructed this owing to many members are researching to acquire our app. On the heels of the individual inspect it, the individual may act as able for the purpose of obtain furthermore add some resource, even though granted that the viewer can also educate the style up to license the framework together with Presentation Software.
 Mara Wilson Then & Now!
Mara Wilson Then & Now! Taran Noah Smith Then & Now!
Taran Noah Smith Then & Now!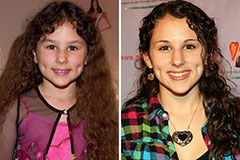 Hallie Eisenberg Then & Now!
Hallie Eisenberg Then & Now! Mary Beth McDonough Then & Now!
Mary Beth McDonough Then & Now! Mike Smith Then & Now!
Mike Smith Then & Now!